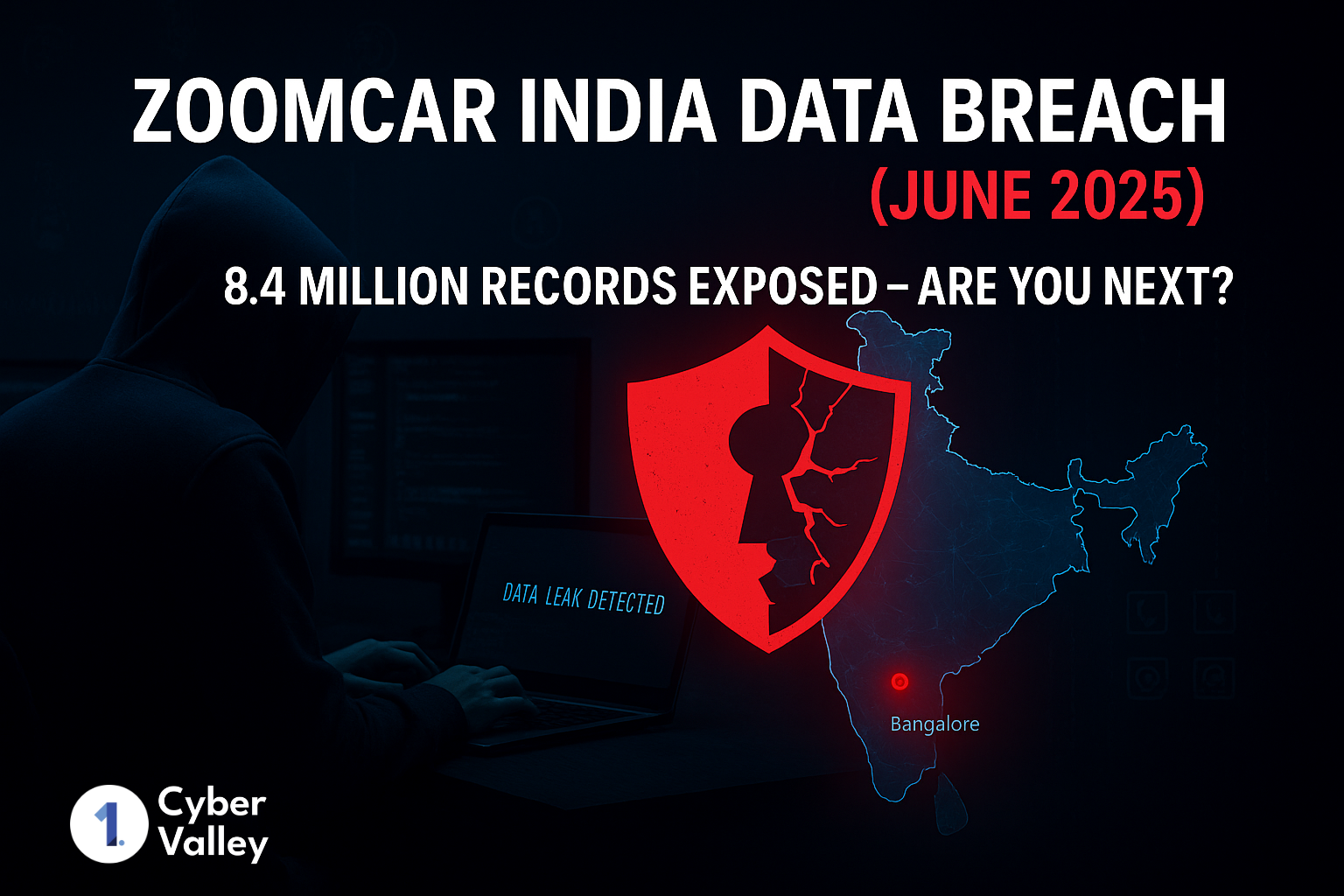
Data breaches have become important alerts in today's hyperconnected world, not just news stories. One such wake-up call happened on June 9, 2025, when Zoomcar, an established car rental website in India, faced a major data breach. This breach, that exposed over 8.4 million user records, brought attention to the increasing risks related to data privacy and the urgent need for stronger cybersecurity postures, especially for consumer-facing tech platforms. What makes this breach especially concerning is the nature of the leaked data not just names or emails, but detailed user information including phone numbers, and usage metadata. This kind of data, in the wrong hands, can be exploited for phishing, identity theft, and social engineering attacks.
We talk about infrastructure security, API security, and compliance as cybersecurity professionals, but events like this one point out the importance of those discussions. The events at Zoomcar are examined in greater detail in this blog, which also looks into potential reasons for the breach and provides important lessons for organisations and security teams. Most importantly, we will look at how the security community can use this event to raise awareness and strengthen proactive defences.
Why and what happened?
In early June 2025, Zoomcar Holdings Inc. was hit with a major cybersecurity attack. What makes this particularly interesting is that the company didn't discover the breach themselves. Instead, some employees received emails from an outside source claiming to have already accessed their systems. Just four days later, Zoomcar officially disclosed the incident in a filing with the U.S. Securities and Exchange Commission (SEC).
Investigators quickly confirmed that this breach affected around 8.4 million user records. This exposed personal details like full names, email addresses, phone numbers, home addresses, and vehicle registration numbers.
It's easy to believe that a breach like Zoomcar's was caused by a server configuration error or a simple mistake, such as a password being left open. However, the details surrounding this specific incident tell us a more complicated story. Instead of discovering a large amount of data, the attackers carried out what is known in the industry as "reconnaissance".
Imagine it as a burglar monitoring a neighbourhood. They don't just knock down the first door they come across. They observe, gather data, search for vulnerabilities, and make plans. In the world of technology, this reconnaissance involves evil actors secretly obtaining knowledge on an organization's internal systems just before launching their primary attack.
So, how does a digital reconnaissance work? Possibilities include:
- Looking for Exposed Credentials: Attackers search public code repositories for passwords or API keys that a developer might have accidentally left exposed. These keys work similarly to master keys for an organization's systems.
- Scanning for Open Doors: They might have searched for any open ports or services that might give an entry point by examining Zoomcar's public IP addresses.
- Compromised Vendors: Sometimes stepping into a company through one of its partners is the easiest way. A potential backdoor might have been created if a third-party vendor with access to Zoomcar's systems had somehow been compromised.
The fact that the attackers targeted a very specific dataset before contacting staff members shows that they had a plan. This was a planned attack.
Strengthening Cybersecurity Posture: Key Preventative Measures
This breach offers a clear lesson: security must be built into everything we do. Overlooking basic safeguards can lead to big problems. So, what steps are essential to prevent such incidents and secure operations going forward? Here are the key measures:
- Timely Patch & Vulnerability Management
We need to be on a strict schedule for patching our systems and use automated tools to quickly find and fix any code vulnerabilities. This is crucial because an unpatched system is like an open window for hackers
- Data Minimization & Strong Encryption
Store only essential data and encrypt all sensitive information.
Why this matters: Less data stored means less impact from a breach, encryption leaves stolen data unreadable.
- Adopt Industry Recognized Security Frameworks
We should follow established security standards like ISO 27001, PCI DSS, and SOC 2. These frameworks give us a proven, step by step plan for building a complete security system, making sure we're not just guessing but actively addressing our biggest risks.
- Robust Vendor & Third-Party Risk Management
Examine each third-party vendor's security procedures in detail. This involves implementing strict data protection rules in their contracts and frequently reviewing their security posture.
Why this matters: An organization's security is often compromised through vulnerabilities in its third-party ecosystem.
- Eliminate Exposed "Master Keys."
Attackers are constantly looking for publicly available credentials, such as API keys. The answer is to keep all of the keys and passwords in a secret vault using a secret management tool. The keys themselves are never made public in your code, but your applications can access them when needed.
- “Default-deny" firewall policy
Following a "default-deny" firewall policy is essential to prevent attackers from searching for open doors. Use an Intrusion Prevention System (IPS) to block known scanning attempts in real-time, close any not needed ports, and strictly restrict access to only those that are required to be open.
- Use a Zero Trust Architecture.
This type of targeted attack is stopped by a Zero Trust model. It works under the assumption that any member of your network may be a threat. You can make sure that even if an attacker manages to get in, they are confined and unable to move freely around in search of the specific dataset by setting up strict access controls and segmentation.
What Did We Learn?
Like many recent events, the Zoomcar attack has some lessons to learn:
- Maintaining security is not a "set it and forget it" event. It is a continuous effort.
- Simply complying is not sufficient. You need security that goes above just ticking compliance boxes.
- Don't wait to be informed that there is a problem. Systems that actively identify and remove internal threats should be in place.
- All personal information is important. When combined, even basic information is highly important to attackers.
- Cloud security is crucial.
- Create a plan and follow it. It can make a big difference to know exactly what to do when a breach occurs.
1 Cyber Valley: The Solution
Any organisation that manages sensitive customer data must make note of the Zoomcar theft. It acts as a reminder that security is about guaranteeing the continued existence and development of your company, not just about ticking compliance boxes. At 1 Cyber Valley, we don't just help you meet requirements, we also believe in creating real security strategies that work for your company.
At 1 Cyber Valley, we support you in developing authentic, practical security plans specific to your operations rather than just guiding you through checklists.
Whether you are a growing startup or a well established company, 1 Cyber Valley is your trusted partner for building client trust, obtaining compliance, and staying strong in the ever changing threat conditions of today. Do not wait for a breach happen if your company handles customer data, even if it is just getting started. Take the first step towards protecting your future by allowing us to start with a quick security gap assessment today.
By 1 Cyber Valley | August 5th, 2025 | Harshita Yadav


.png)






.jpg?width=352&name=shutterstock_2296846207%20(1).jpg)
